Hey folks, in the last 8 years I have been helping a lot of companies to deploy what is now known as BeyondTrust Privilege Management for Windows (PMfW) and was formerly known as Avecto Defendpoint or Privilege Guard. In this post, I want to show you how to harden your Group Policy based configurations against unwanted access.
Problem
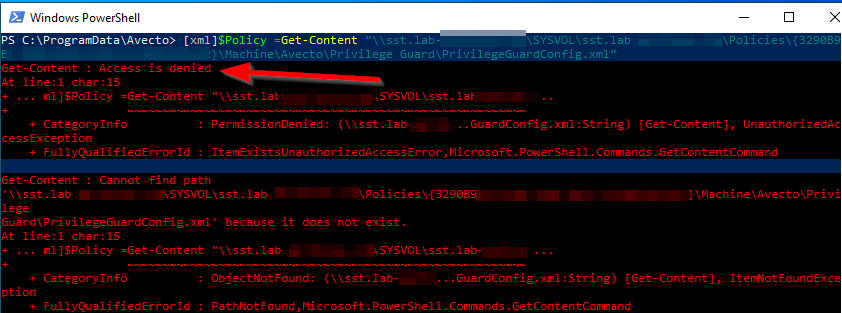
The PMfW Agent uses a human-readable XML configuration file which in most cases is deployed via Group Policy. The locally cached configuration is protected against unelevated access with NTFS permissions, but this does not apply to the default configuration of the Group Policy. The XML configuration file stored in the policy directory in the SYSVOL-Share of the Domain is readable for every authenticated user. A clever user or an attacker could use read-only access to find a loophole in the configuration to elevate processes he is not allowed to or to gain full admin access to the computer. It is very unlikely, due to the Anti-Tampering mechanisms implemented into the Agent, but not impossible.
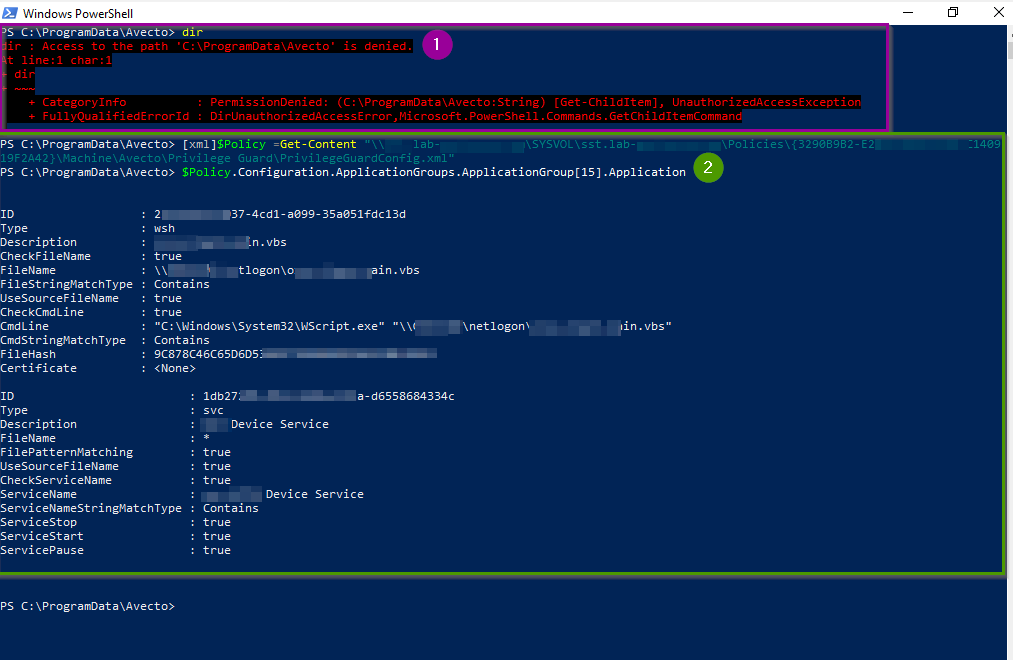
As you can see in the picture above access to the local policy cache in %ProgramData%\Avecto is prohibited (1). But the user can load the XML configuration file from the GPO folder in the SYSVOL-Share and for example, look up the application definitions of an Application Group (2).
Solution
If you are only using computer policies for PMfW, which is quite common, the solution is easy. Just replace the Authenticated Users entry in the Security Filtering of the relevant Group Policies with the Domain Computers group.
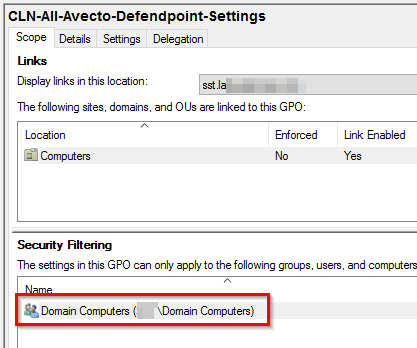
Changing the Security Filtering of a GPO is the same as setting NTFS permissions on the folder of the policy in the SYSVOL-Share. As you can see in the picture below accessing the GPO from the network is no longer possible for the user. However, the System Account of the device, which is automatically part of the Domain Computers group of the Active Directory Domain, is still able to access it during policy updates.